
Microsoft warns that attackers are deploying malware in ViewState code injection assaults utilizing static ASP. NET machine keys discovered on-line.
As Microsoft Menace Intelligence specialists lately found, some builders use ASP.NET validationKey and decryptionKey keys (designed to guard ViewState from tampering and data disclosure) discovered on code documentation and repository platforms in their very own software program.
Nonetheless, risk actors additionally use machine keys from publicly out there sources in code injection assaults to create malicious ViewStates (utilized by ASP.NET Net Varieties to regulate state and protect pages) by attaching crafted message authentication code (MAC).
When loading the ViewStates despatched through POST requests, the ASP.NET Runtime on the focused server decrypts and validates the attackers’ maliciously crafted ViewState knowledge as a result of it makes use of the correct keys, hundreds it into the employee course of reminiscence, and executes it.
This enables them to execute code remotely on the IIS server and deploy extra malicious payloads.
In a single occasion noticed in December 2024, an unattributed attacker used a publicly recognized machine key to ship the Godzilla post-exploitation framework, which comes with malicious command execution and shellcode injection capabilities, to a focused Web Info Providers (IIS) net server.
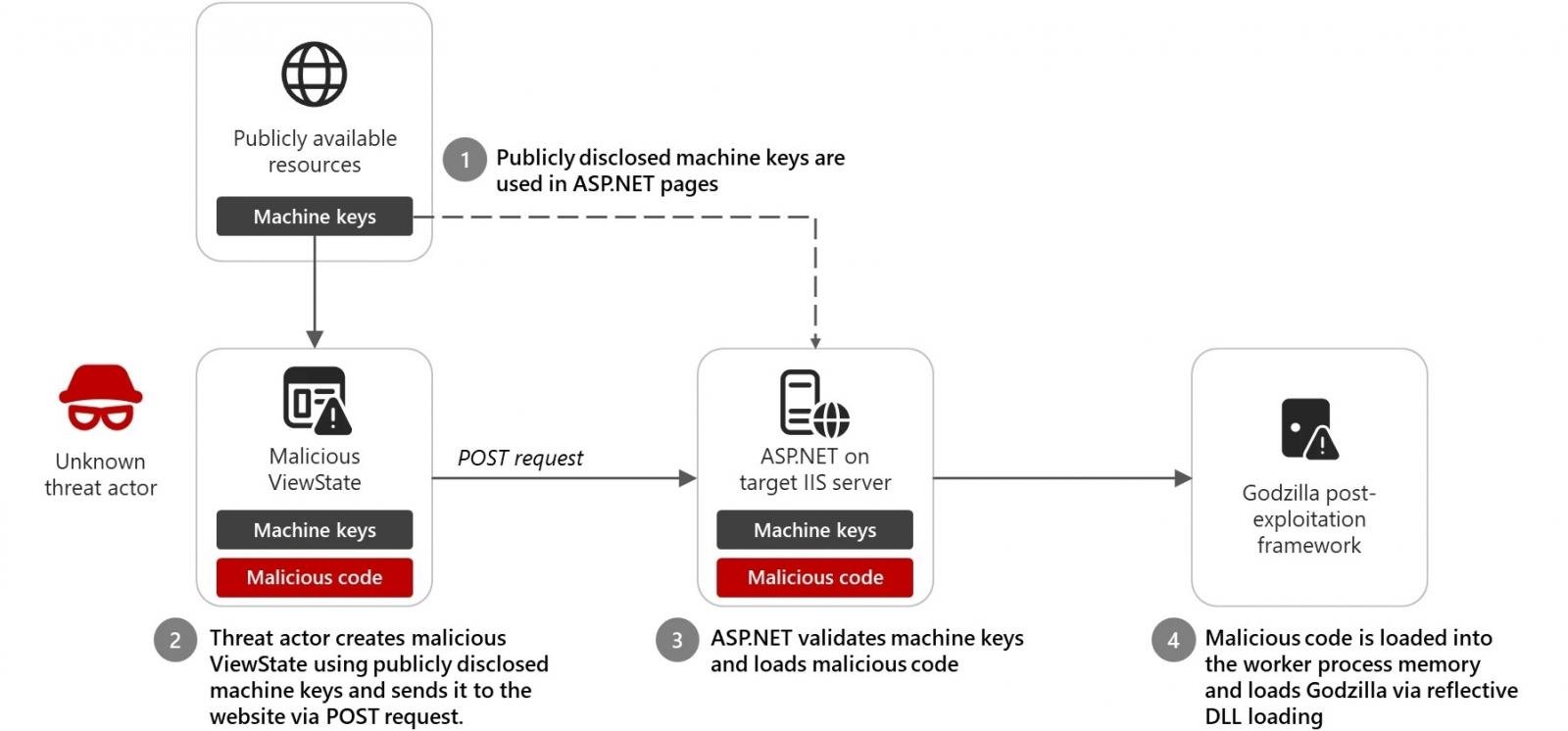
“Microsoft has since recognized over 3,000 publicly disclosed keys that may very well be used for all these assaults, that are known as ViewState code injection assaults,” the firm mentioned on Thursday.
“Whereas many beforehand recognized ViewState code injection assaults used compromised or stolen keys which might be typically bought on darkish net boards, these publicly disclosed keys might pose a better danger as a result of they’re out there in a number of code repositories and will have been pushed into improvement code with out modification.”
To dam such assaults, Microsoft recommends builders securely generate machine keys, not use default keys or keys discovered on-line, encrypt machineKey and connectionStrings components to dam entry to plaintext secrets and techniques, improve apps to make use of ASP.NET 4.8 to allow Antimalware Scan Interface (AMSI) capabilities, and harden Home windows Servers by utilizing assault floor discount guidelines reminiscent of Block Webshell creation for Servers.
Microsoft additionally shared detailed steps for eradicating or changing ASP.NET keys within the net.config configuration file utilizing both PowerShell or the IIS supervisor console and eliminated key samples from its public documentation to additional discourage this insecure apply.
“If profitable exploitation of publicly disclosed keys has occurred, rotating machine keys won’t sufficiently deal with doable backdoors or persistence strategies established by a risk actor or different post-exploitation exercise, and extra investigation could also be warranted,” Redmond warned.
“Specifically, web-facing servers needs to be absolutely investigated and strongly thought-about for re-formatting and re-installation in an offline medium in instances the place publicly disclosed keys have been recognized, as these servers are most prone to doable exploitation.”